Compromised IAM credentials
Scenario 2: Compromised IAM credentials
You have completed the first attack simulator and are back with your cup of coffee. However, you continue to receive new notifications about Findings related to AWS IAM services. The body of the first message indicates that using IAM credentials, some API calls were made from the IP address that was added to the Threat List (in this post). before).
No individual IAM credentials have ever been exposed or disclosed in any way.
Content
Architecture Overview
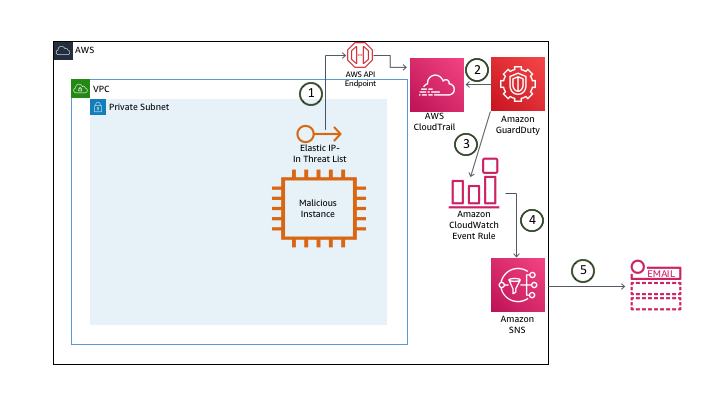
- This EC2 malicious instance makes API calls, the EIP of this instance has been added to Threat List. The contents of API calls are logged in CloudTrail’s logs.
- GuardDuty observes the logs of CloudTrail Logs along with VPC Flow Logs and DNS Logs, thereby assessing the situation on certain bases.
- GuardDuty generates corresponding Findings and simultaneously sends details to GuardDuty Console and EventBridge Events.
- EventBridge Event Rule activates SNS Topic.
- SNS Topic sends out E-mail notifications with related information.
Investigation process
Go to GuardDuty Console
To conduct a review of the Findings:
- Access GuardDuty Console at us-west-2
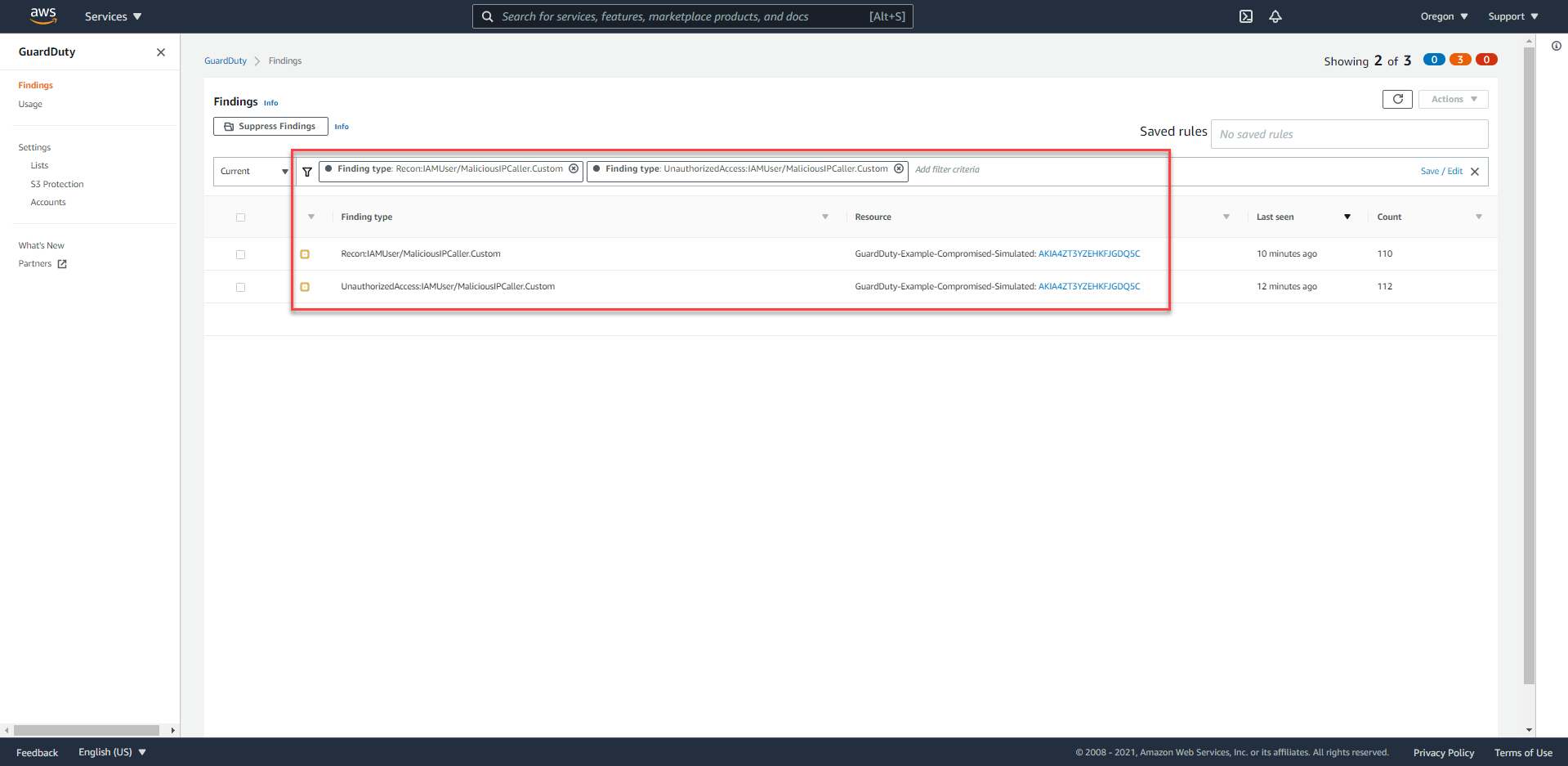
- We will see the Findings in the following format.
Recon:IAMUser.UnauthorizedAccess:IAMUser.
-
If there isn’t any Finding, proceed to press the Refresh button and wait.
-
From Finding -
Recon:IAMUser/MaliciousIPCaller.Custom, we can easily retrieve the following information:- What happened?
- What AWS resources are affected?
- When did this event happen?
-
Under the Resource Affected section, you will find the
User Namerelated to this Finding.
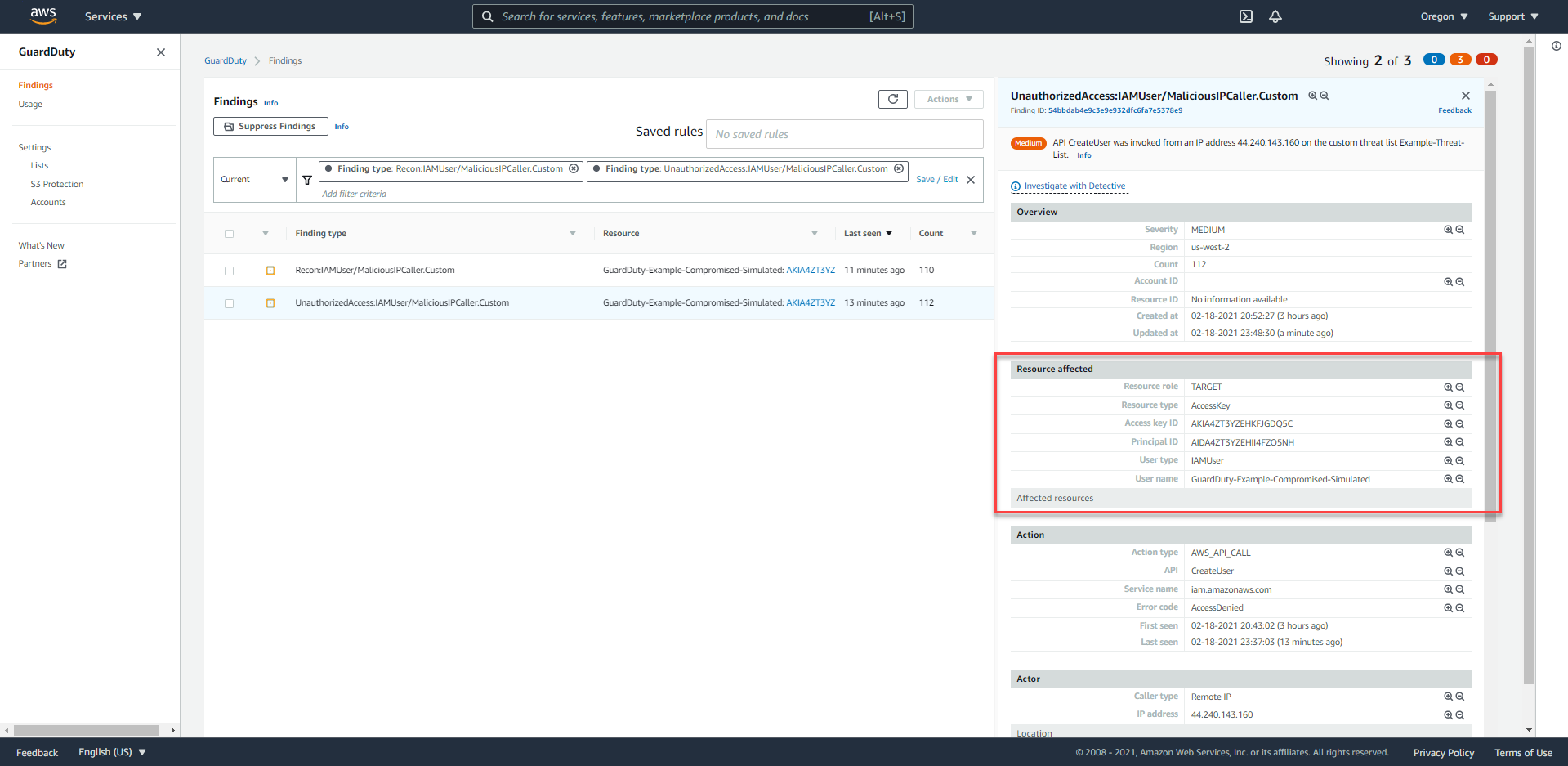
Based on the format reviewed in detail in the previous section, what security incident can you pinpoint through the Finding style?
This finding indicates that the IAM credential of the above User Name could have been exposed by API calls derived from an IP address that was previously added to the Threat List.
What actions were taken by this IAM User?
In the Action section, we see that the DescribeParameters action has been performed.
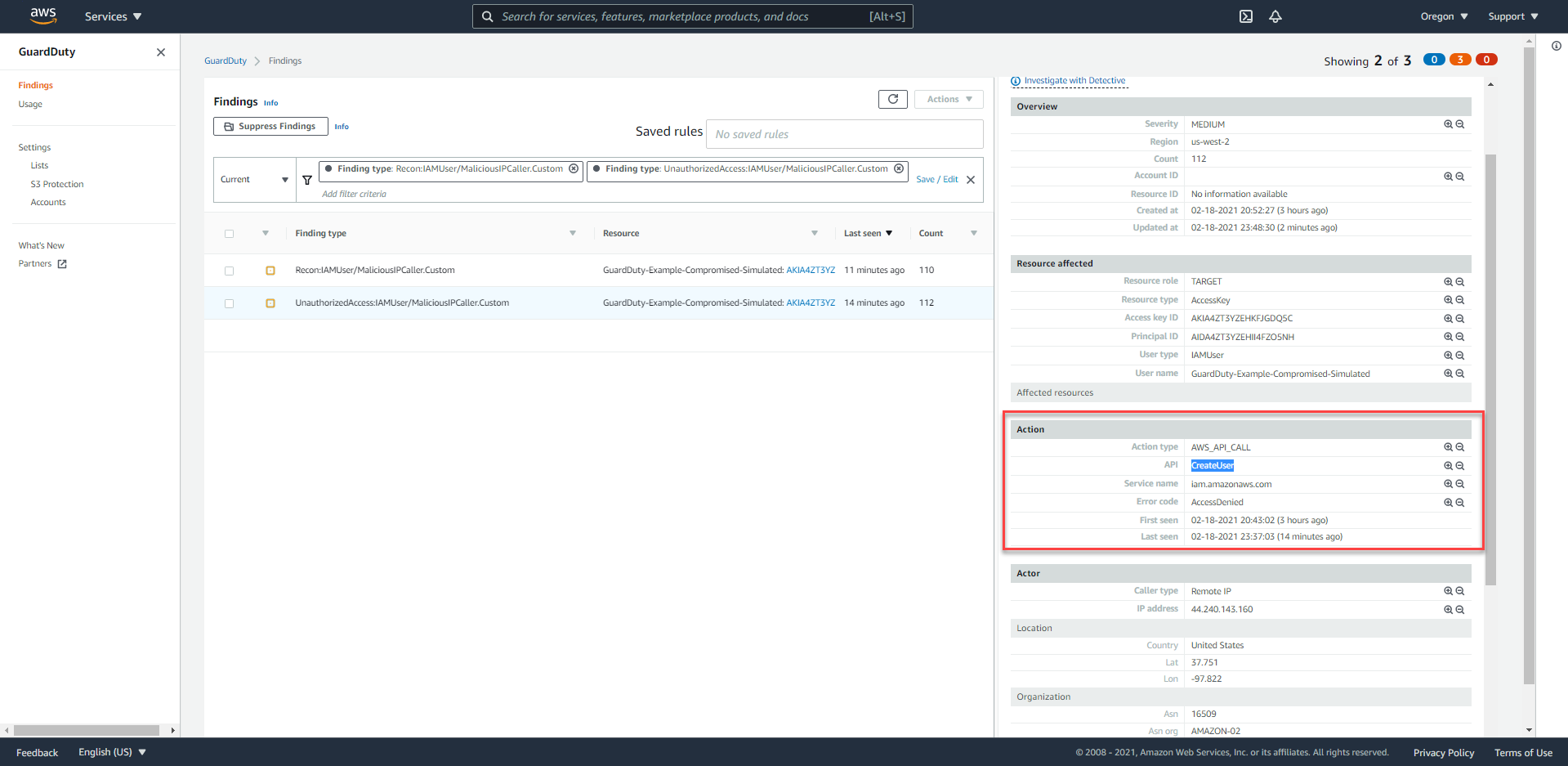
How can we see all the remaining actions, taken by this IAM User, within the last 1 hour or 1 day ago?
GuardDuty is capable of analyzing large amounts of data to pinpoint the hazards present in your environment. However, during the investigation and remediation steps, we also need to combine many different data sources to have the most correlated view possible.
In this case, the analyst can use insights that can be found in user behavior logs through CloudTrail.
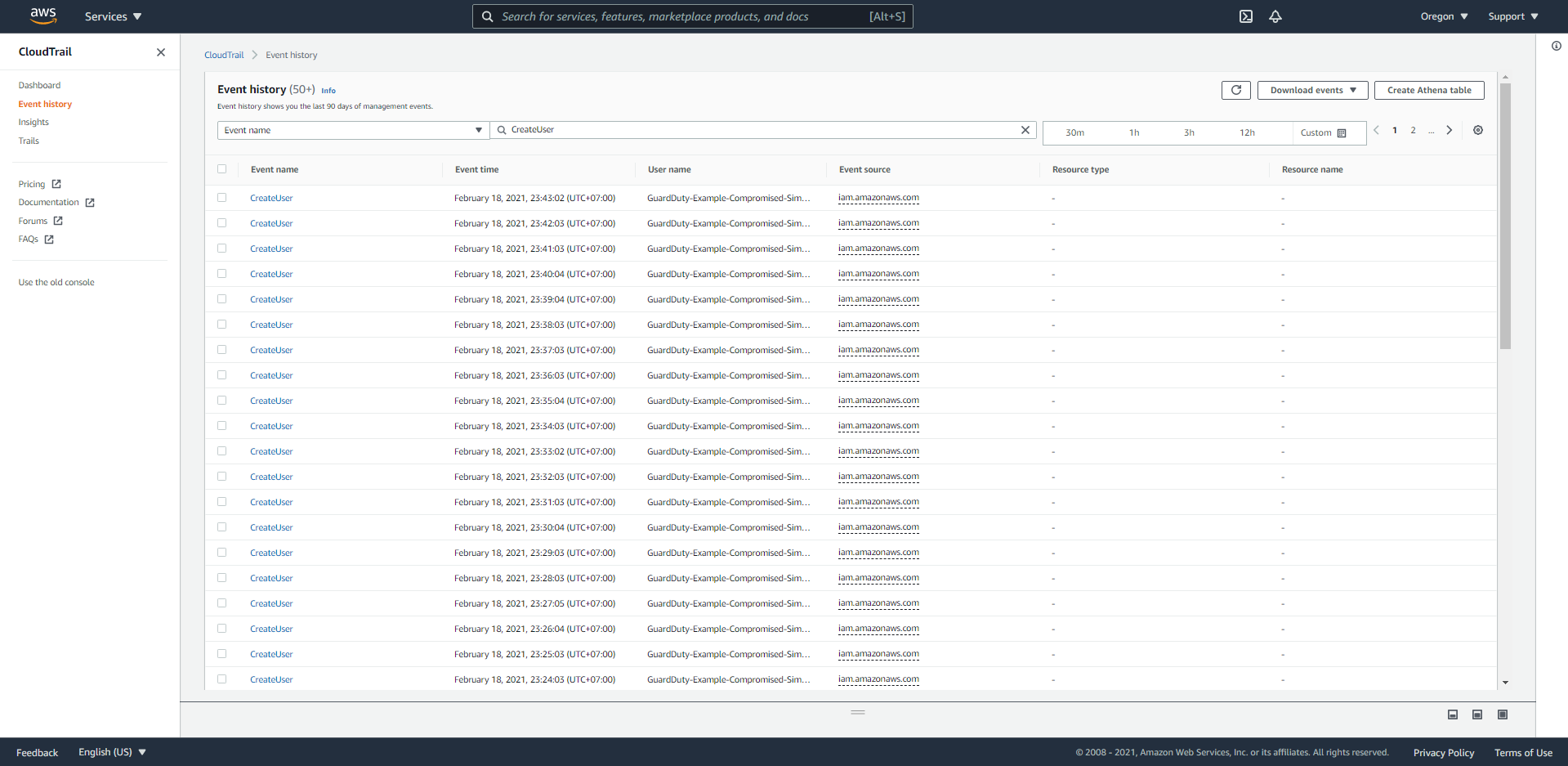
IAM Findings generated by EC2 malicious instance that made API calls and the EIP of this instance are in Custom Threat List.
Check EventBridge Event Rule
- Access the CloudWatch Console at us-west-2.
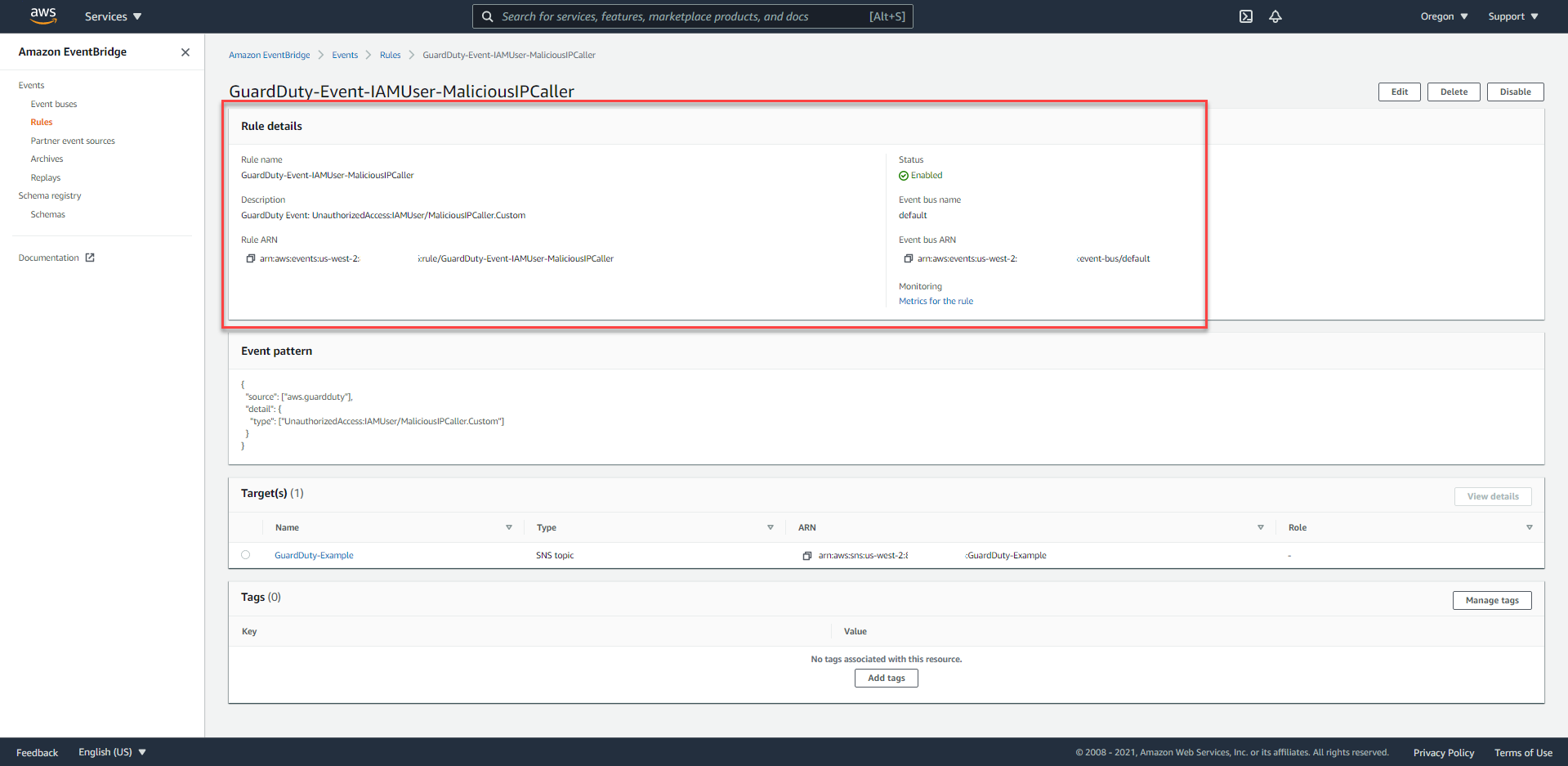
- In the left-hand navigation bar, under Events, select Rules. You will see 3 rules have been set up (by CloudFormation Template), starting with a prefix of the following from
GuardDuty-Event.. - Proceed to select the rule named
GuardDuty-Event-IAMUser-MaliciousIPCaller.
- You will easily notice that there is only one target in the Targets area, which is SNS Topic.
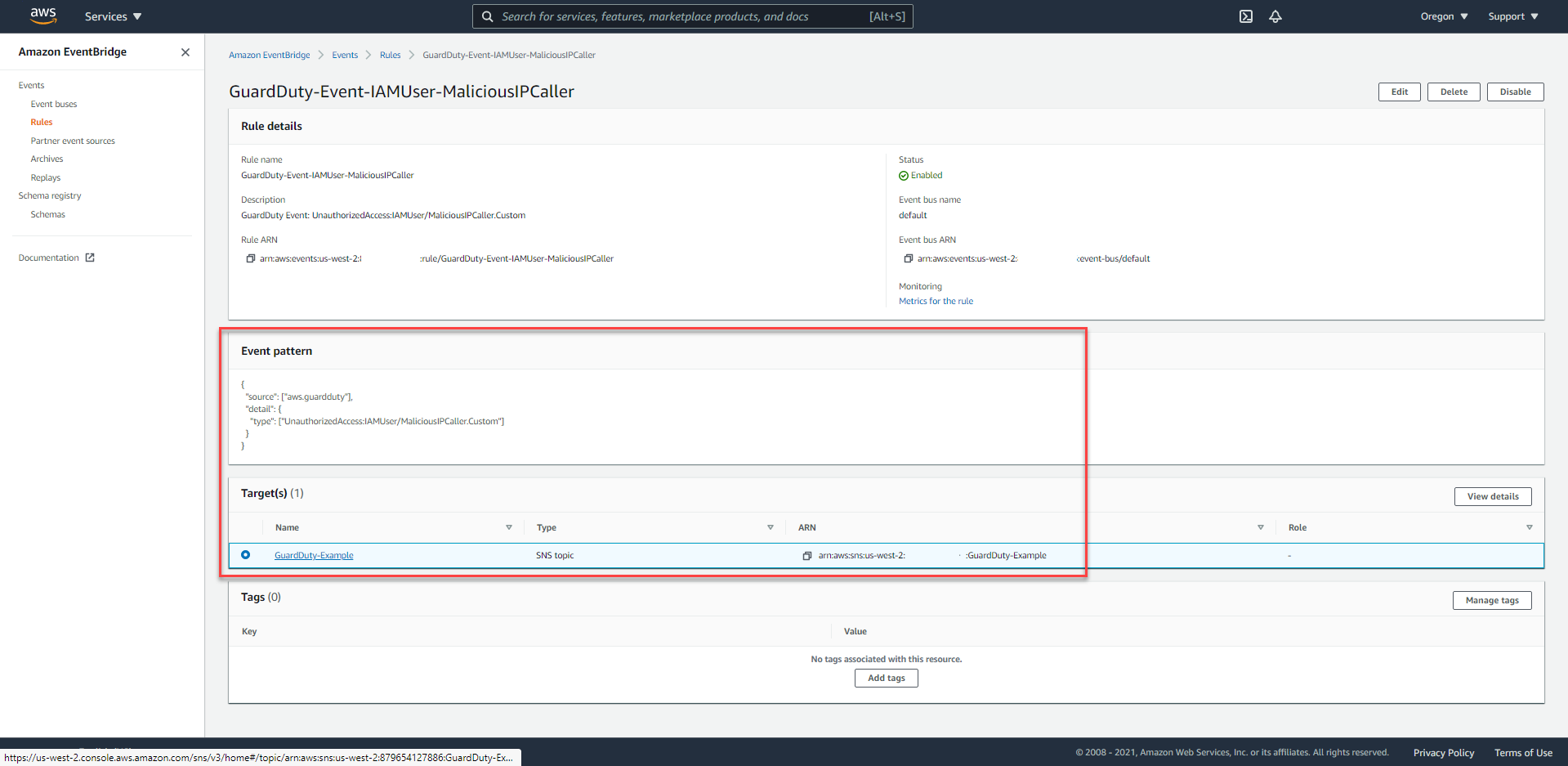
As it turned out, Alice had never set up a Lambda Function to perform the Remediation process because the Security team decided that they would proceed manually with this Finding.
The combination of GuardDuty and EventBridge Events provides flexibility that makes it easy to create an automated Remediation process. Lambda functions or solutions from AWS partners are the top choices.
For certain Findings, we may end up configuring notifications and resolving issues manually, rather than automatically. Because when designing the automation process, we will have to pay attention to and evaluate the results that the Remediation process brings, including advantages and disadvantages.
In addition, we can set Target to some other AWS resources like SSM Run Commands or Step Function State Machine.
Resolve the situation
Since Alice has never set up the Remediation process for this Finding, we need to do it manually. While the Security team is analyzing the behavior of this IAM user to better define the scope of the vulnerability, we need to take some steps to disable Access Key to prevent programming. the next actions.
- Access the IAM Console.
- In the left-hand navigation bar, select Users.
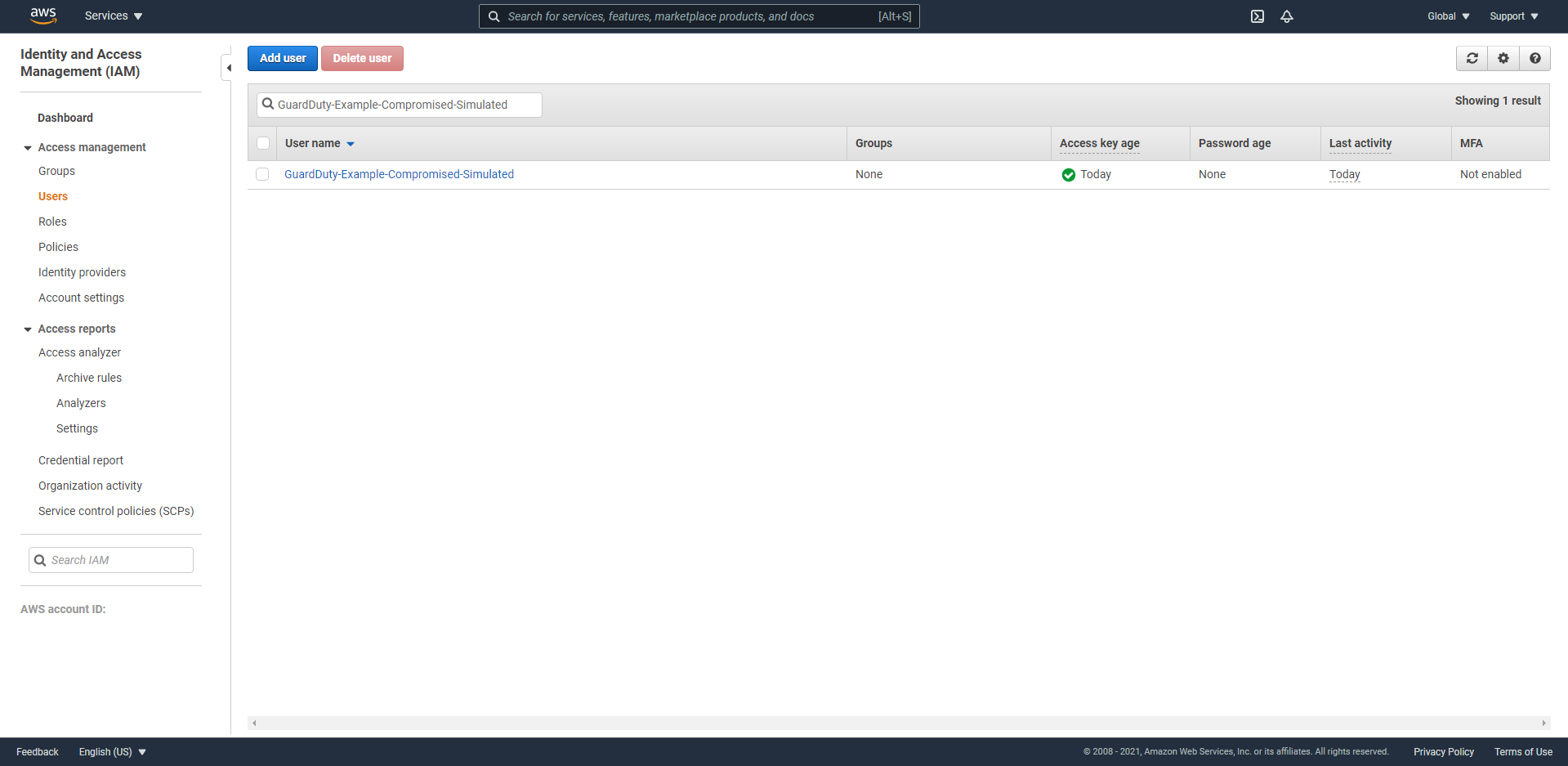
- Based on GuardDuty Finding and E-mail message, we can easily choose IAM user -
GuardDuty-Example-Compromised-Simulated. - In the user
GuardDuty-Example-Compromised-Simulated, we select the Security Credentials bar.
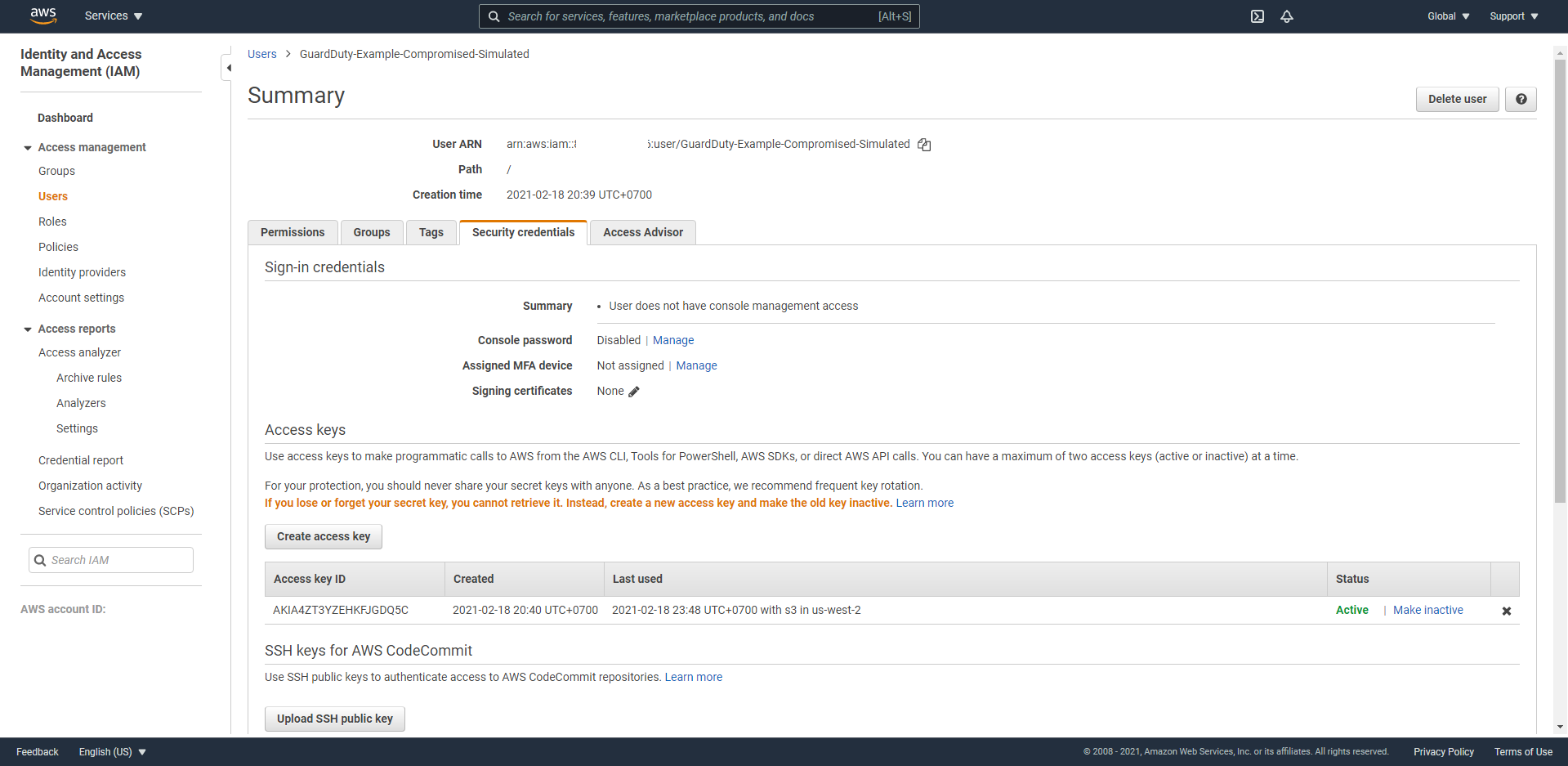
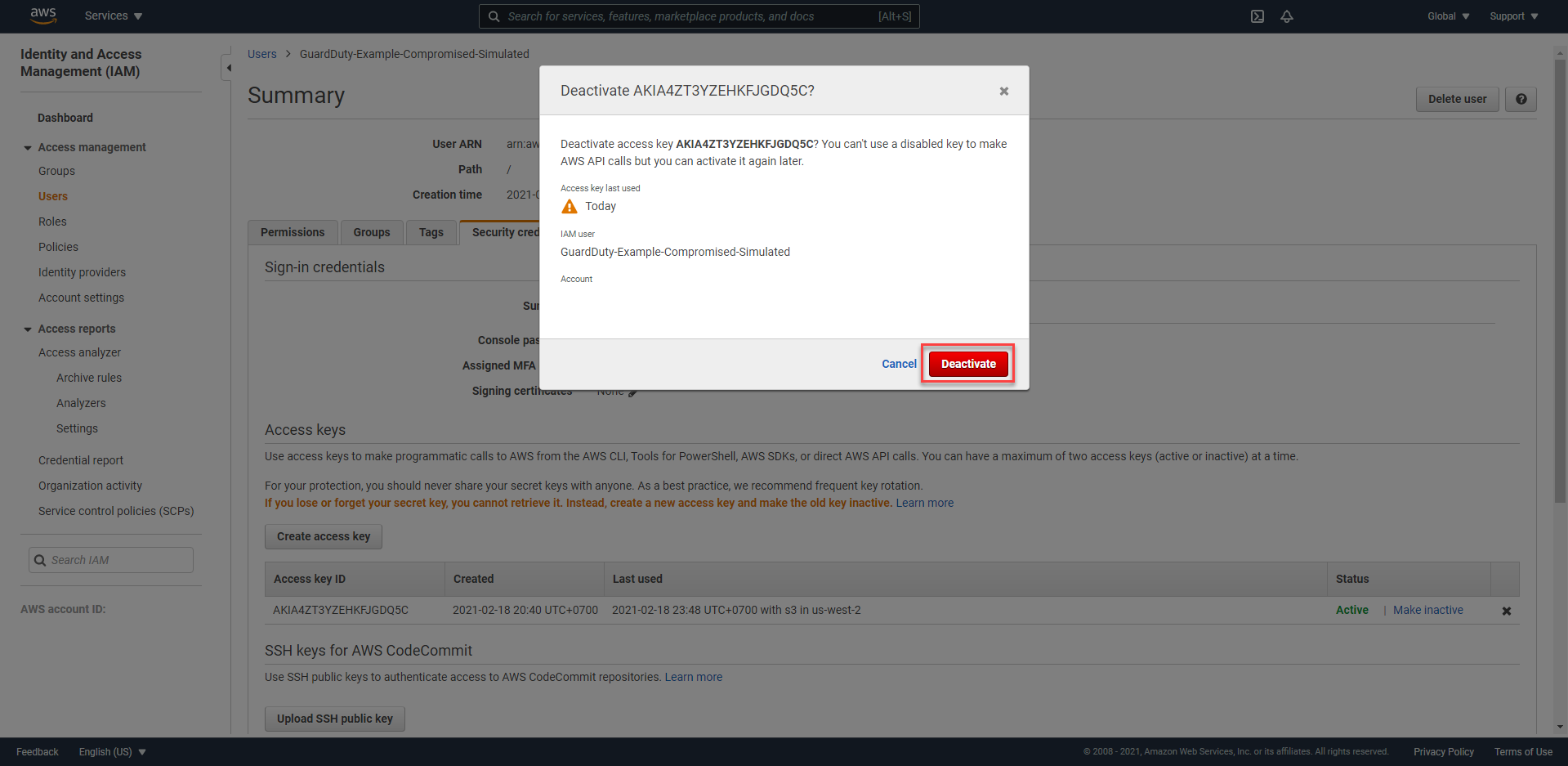
- In the Access Keys section, based on the Access Key ID information from Finding, we proceed to press the
Make Inactivebutton.
Review question
- What data source was used by GuardDuty to identify this threat?
- What Permissions are IAM users allowed to use?
- Why did the Security team decide to go against the automated Remediation process?