Credential Exfiltration
Contents
Architecture Overview
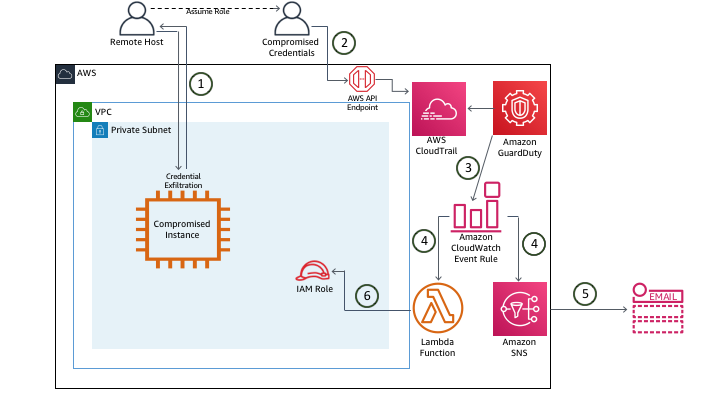
- Remote server accesses EC2 compromised instance and steals IAM role credential through Metadata data.
- This server sets up the AWS CLI Profile to make API calls to the AWS account.
- GuardDuty generates related Findings and sends them simultaneously to the GuardDuty console and EventBridge Events.
- EventBridge Event Rule activates SNS Topic and Lambda Function.
- SNS Topic proceeds to send an E-mail notification with Finding details.
- Lambda Function assigns a new policy to revoke all active Sessions.
Investigation process
Go to GuardDuty Console
To conduct a review of the Findings:
- Access GuardDuty Console at us-west-2
- We will see Findings in the following format -
UnauthorizedAccess:IAMUser/InstanceCredentialExfiltration.
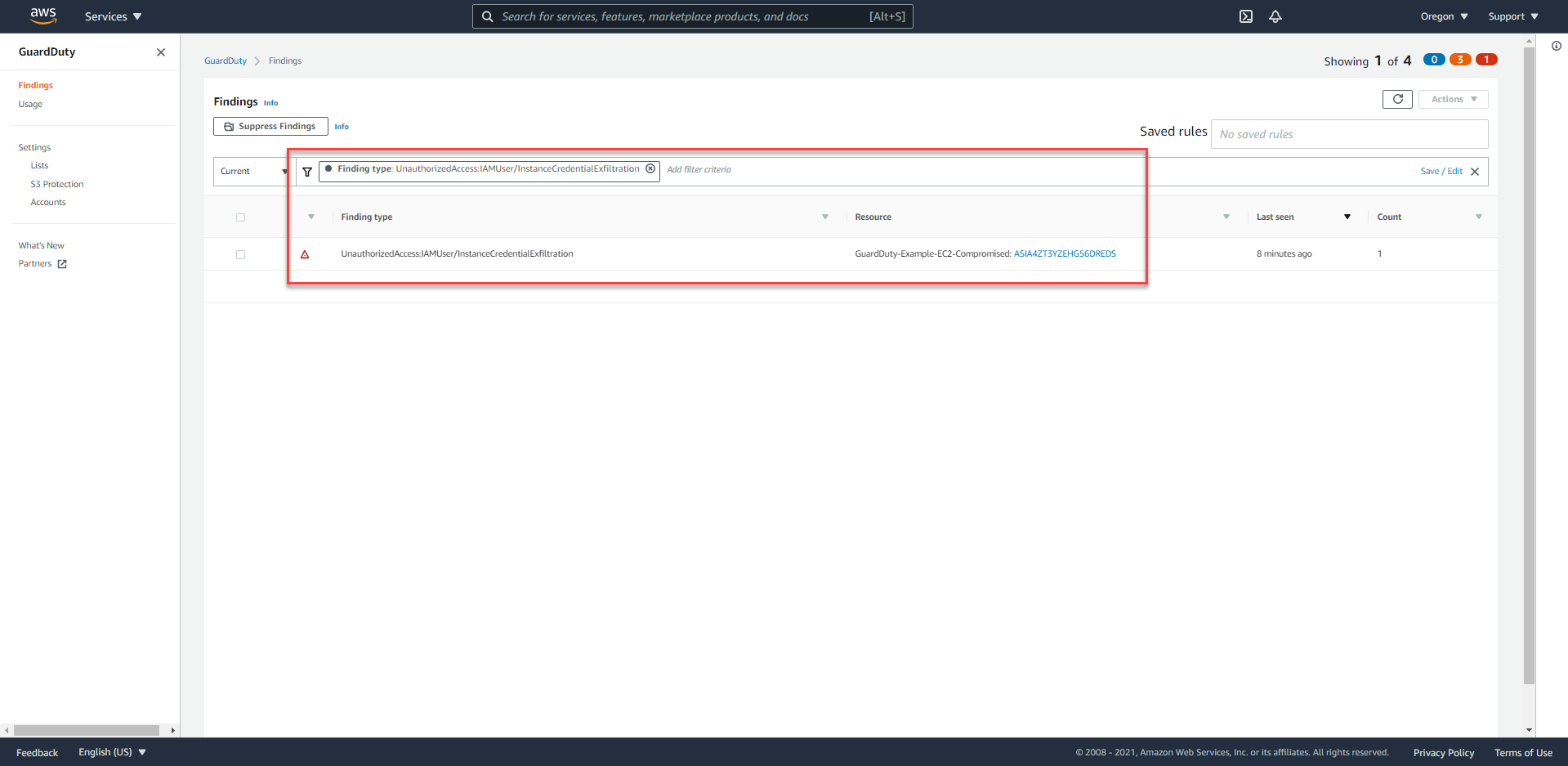
- If there isn’t any Finding, proceed to press the Refresh button and wait.
- From Finding -
UnauthorizedAccess:IAMUser/InstanceCredentialExfiltration, we can easily retrieve some of the following information:- High Severity
- Notice that someone intentionally used the IAM role credential outside the EC2 instance
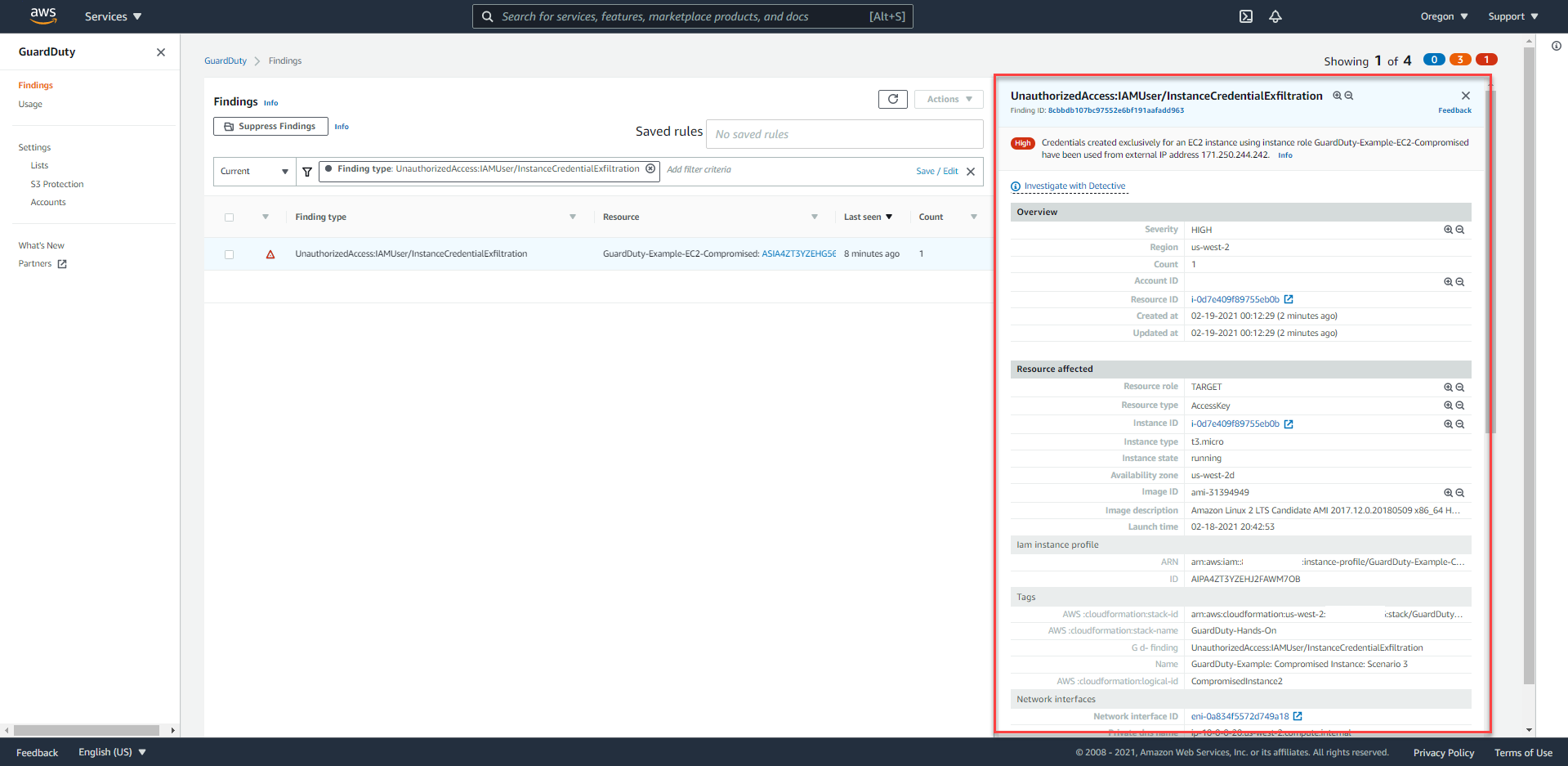
Each GuardDuty Finding will be assigned a specific severity - Low/Medium/High. These levels are defined by AWS, they are used to classify and define
Check EventBridge Event Rule
- Access the CloudWatch Console at us-west-2.
- In the left-hand navigation bar, under Events, select Rules. You will see 3 rules have been set up (by CloudFormation Template), starting with a prefix of the following from
GuardDuty-Event.. - Proceed to select the rule named
GuardDuty-Event-IAMUser-InstanceCredentialExfiltration.
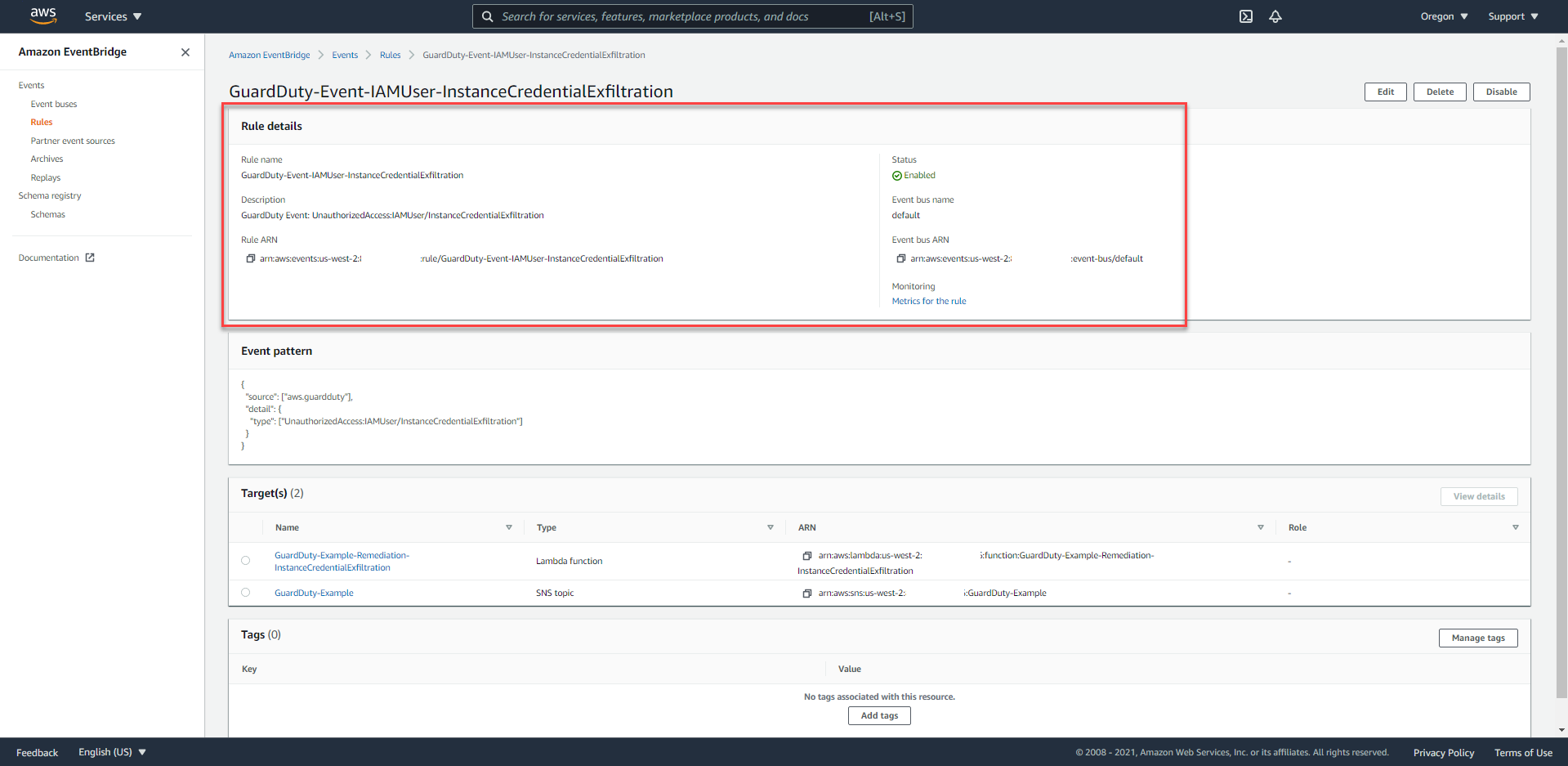
- In the Event Pattern section, we can easily see the data source that this Event will record and proceed to trigger Target when there are any events.
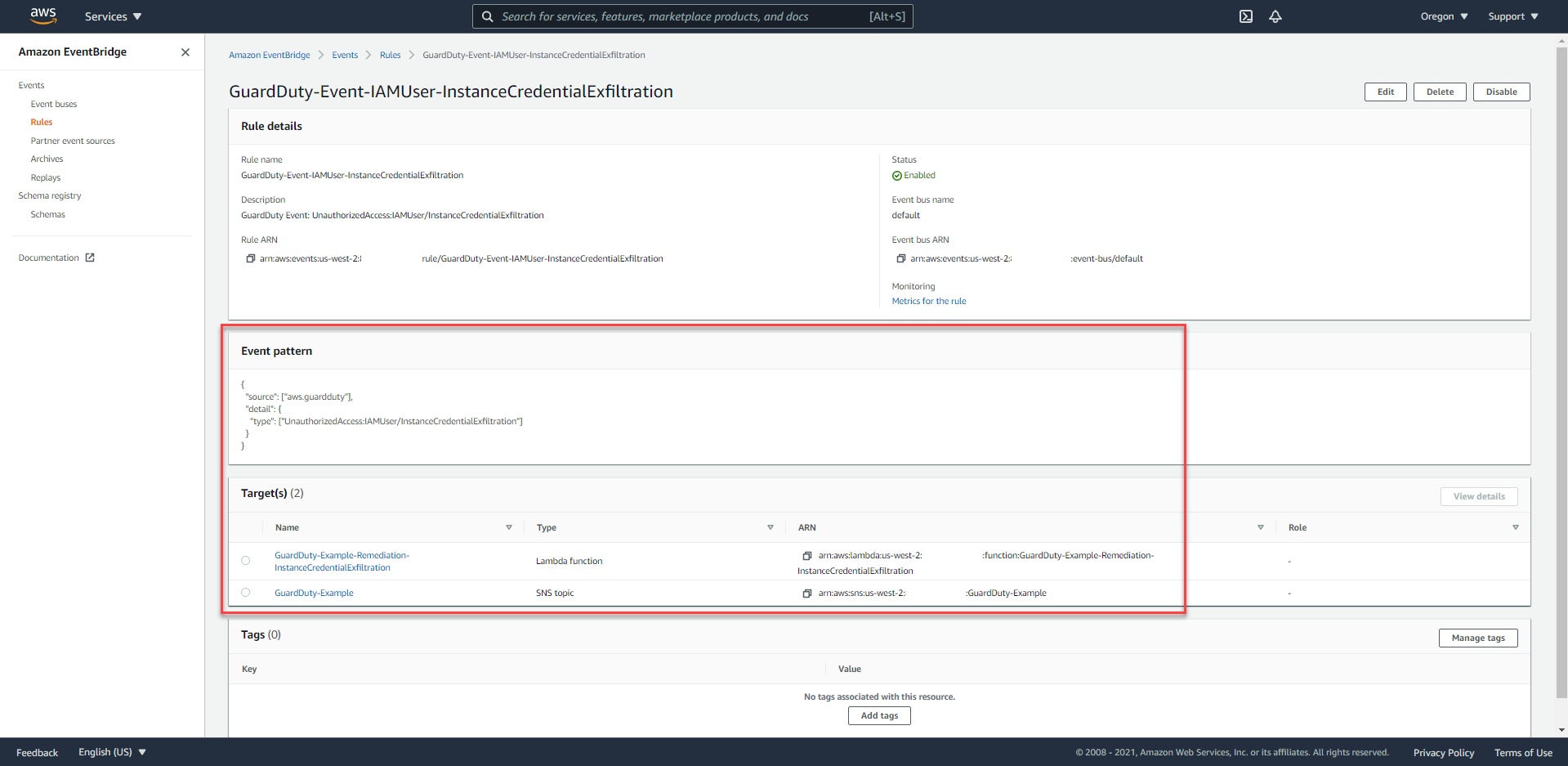
You can create an EventBridge Event Rule to record events of a particular type of Finding or any type of Finding.
The following is an example to document any GuardDuty Findings events.
{
"detail-type": [
"GuardDuty Finding"
],
"source": [
"aws.guardduty"
]
}
Check the Remediation process with Lambda Function
Alice has set up the Remediation process to automatically respond to this threat through the Lambda function. We can check the programmed code to understand more about this process.
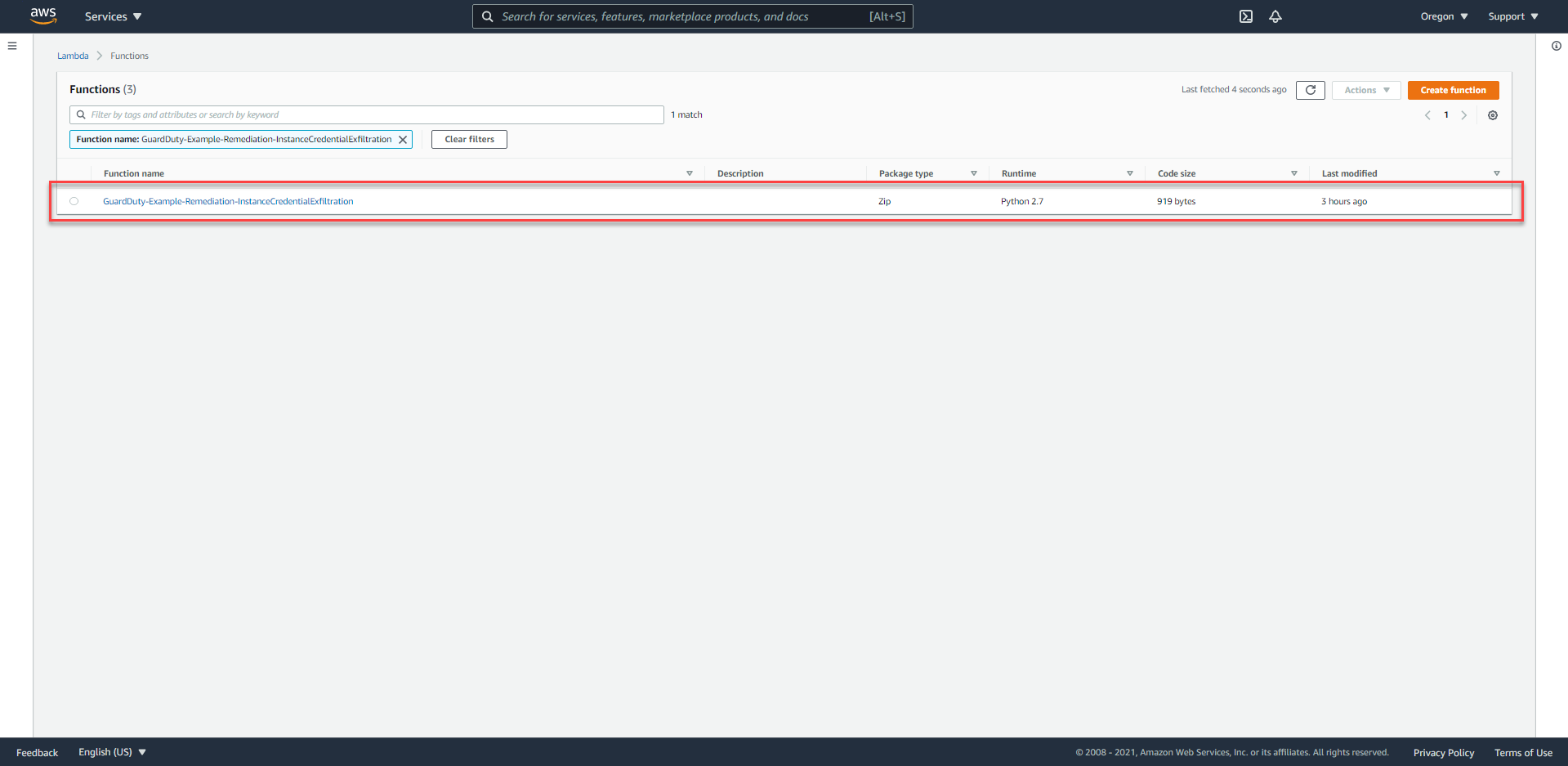
- Access the Lambda Console at us-west-2.
- In the left hand navigation bar, select Functions and search for
GuardDuty-Example-Remediation-InstanceCredentialExfiltration.
- Basically, this Lambda function will retrieve information about IAM Role from Finding and proceed to add IAM Policy.
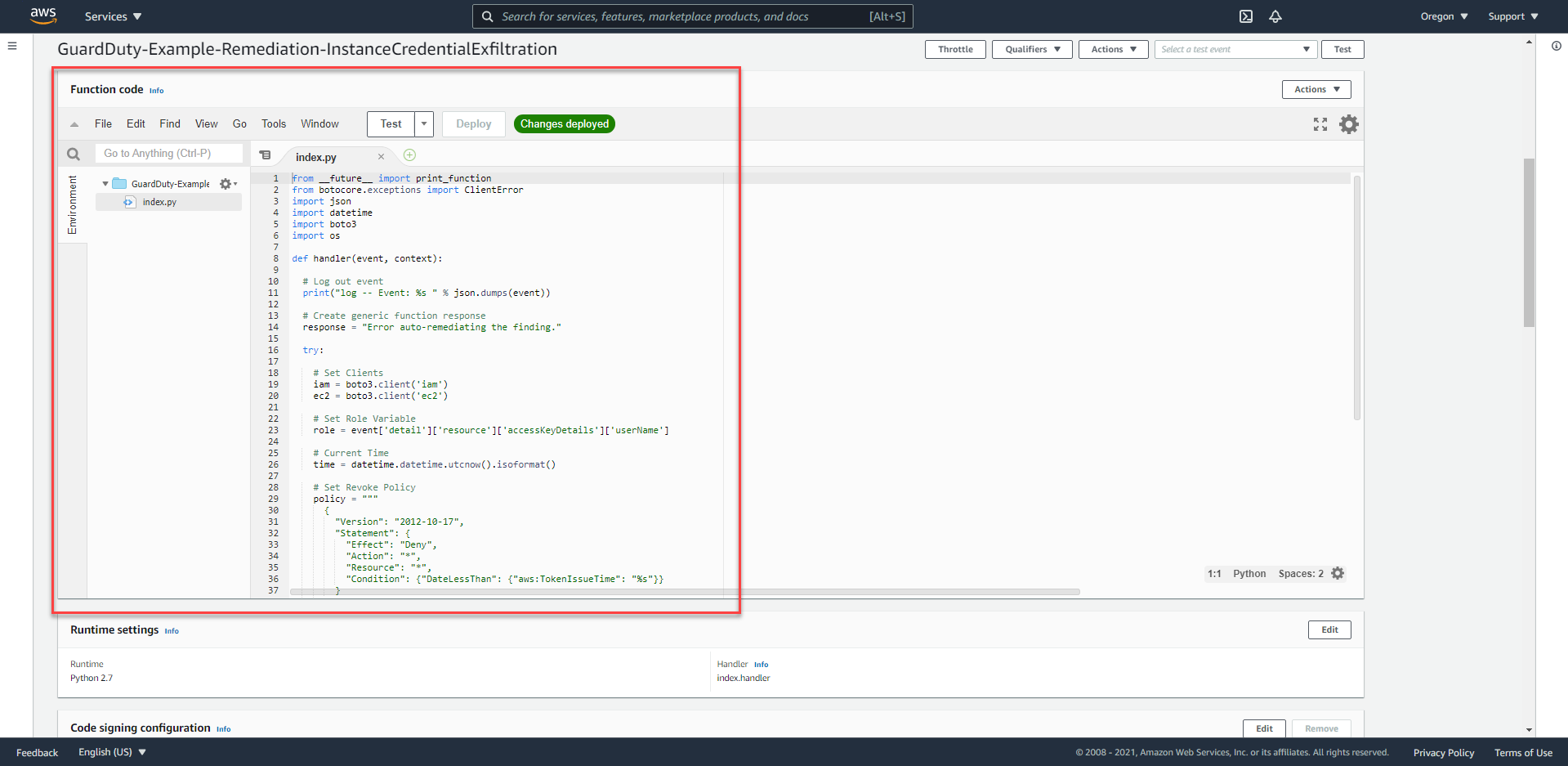
What Permissions does the Lambda Function need to perform the Remediation process? Is there a possible risk with the current Permissions level?
Verify the Remediation Process
To verify that Finding InstanceCredentialExfiltration has been completely resolved, we will proceed with the following steps in turn.
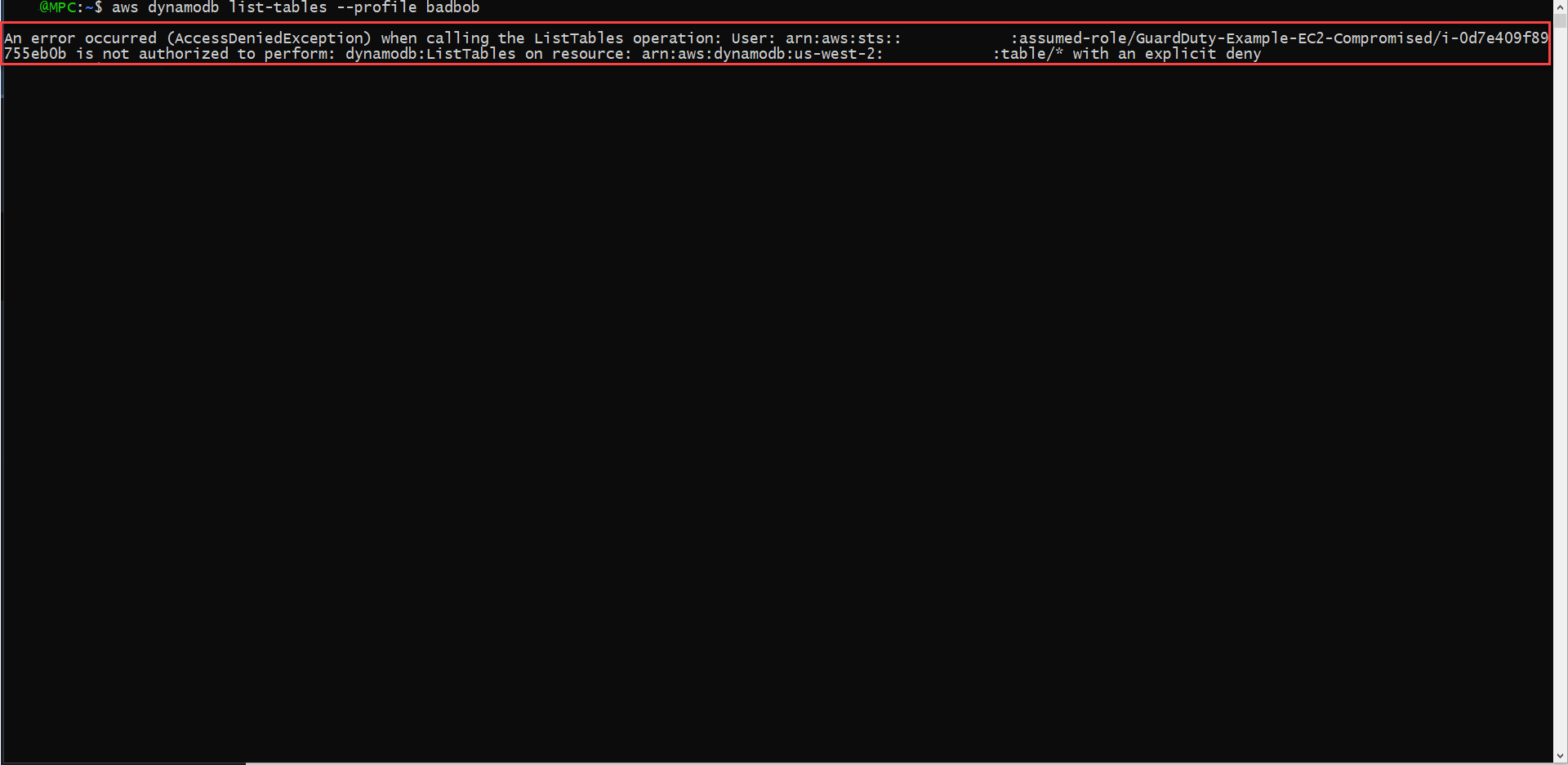
- Verify via AWS CLI
Execute the following command:
aws dynamodb list-tables --profile badbob
We will get AccessDeniedException return for the command to execute.
- Verify via AWS Console
Conduct an evaluation of the IAM Policy that was added to the IAM Role during the Remediation process.
- Access the IAM Console.
- In the left hand navigation bar, select Roles and search for
GuardDuty-Example-EC2-Compromised. This is the IAM Role that we will identify through GuardDuty Finding.
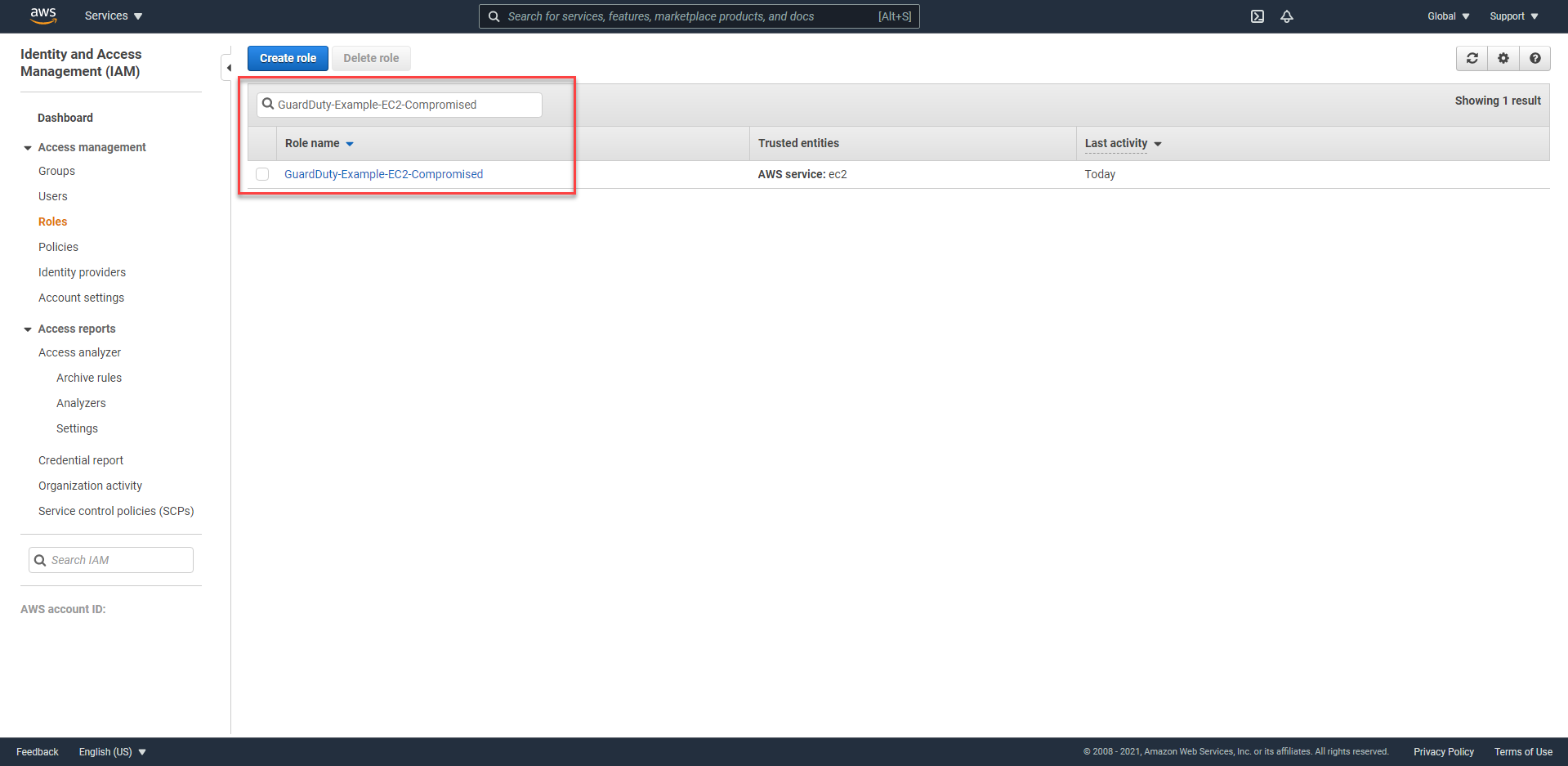
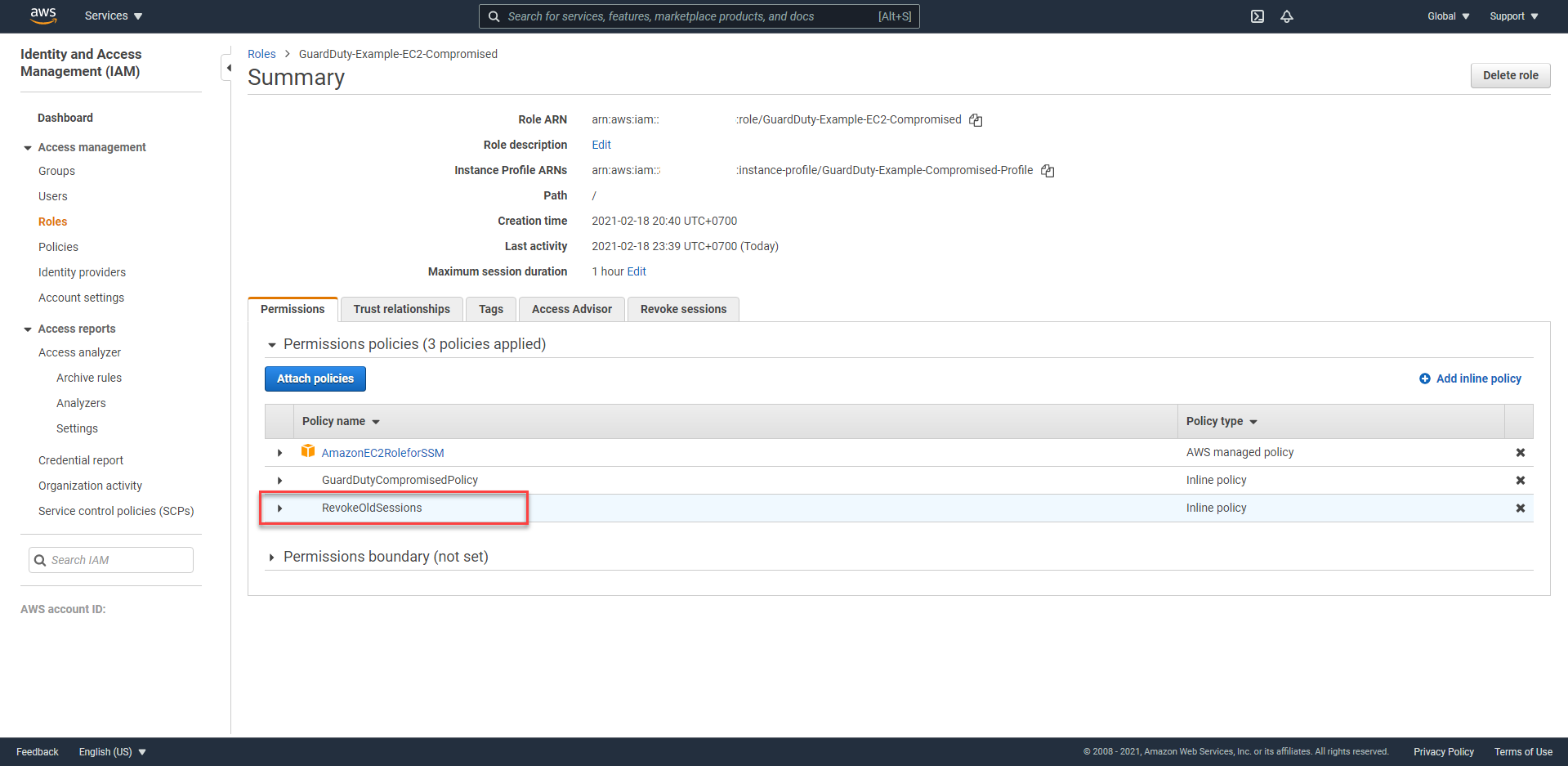
- Click the Permissions bar, click on the IAM Policy
RevokeOldSessions.
Review questions
- What are the risks involved in the Remediation process?
- Are there other EC2 instances that also use this IAM Role?